3. NMAP
Nmap (“Network Mapper”) is an open source tool for network exploration (mapping) and security auditing.
It contains variety of useful tools for network footprinting.
It is used for scanning and information gathering.
It uses raw IP packets in novel ways for the following purposes:
- Identifying hosts
- Operating systems
- Open Ports
- System Vulnerabilities
NMAP commands syntax
sudo nmap [OPTIONS] [TARGET]
- sudo is for root privileges (administrator access).
- Ping Sweeps and active machine identification
Ping sweeps helps to discover computers on your subnet without knowing their IP address.
- Ping is a part of ICMP (Internet Control Message Protocol) software. It works by sending 32 or 56 bytes of data to another host so that host send a response.
It serves two primary purposes:
- To check if the host is available and
- To measure how long the response takes.
- It also help in troubleshooting network connectivity issues ,Network Interface Card functionality and to see which IP addresses are used.
Only active machines would respond to ping unless ping or ICMP is blocked.
Since we cannot ping all the addresses in a subnet tools like nmap can be used to scan for active machines.
Syntax
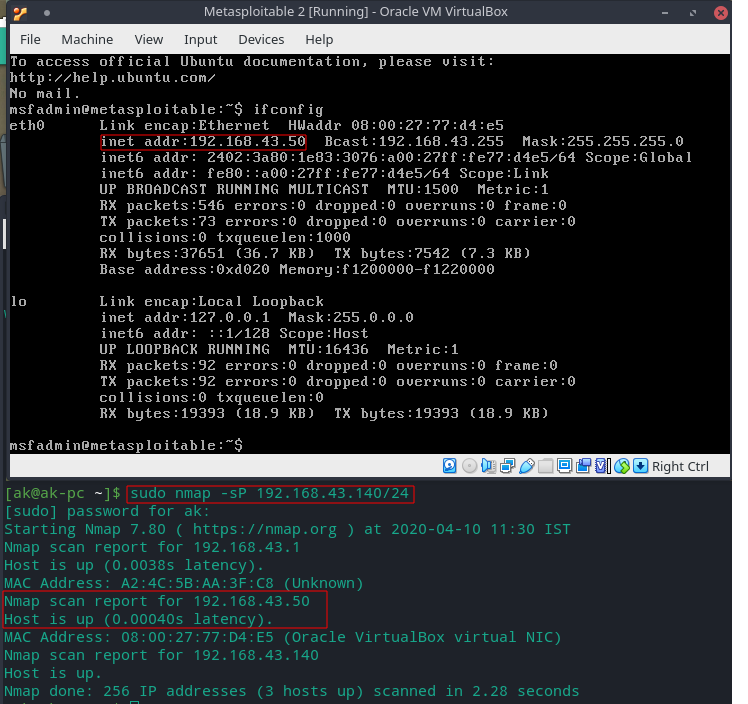
sudo nmap -sP [TARGET]
sudo nmap -sP 192.168.1.0/24
- Here nmap will ping every possible addresses on /24-255.255.255.0 subnet and report which IP addresses responded to the ping to get a list of active machines.
- If ping is blocked or devices do not respond then they will not be available in the result.
We can also scan a single host or other subnets /8,/16 etc
Pinging Metasploitable 2 subent
- Port Scanning
To see the ports on which active hosts are accepting connections. It helps to verify that software firewalls and other security measures are implemented properly. It also helps in understanding the purpose of the active machine for example if a host is accepting connections on port 80 we can assume it’s purpose to be of a HTTP web server or network device with a web interface (router,firewall,access point).
Syntax
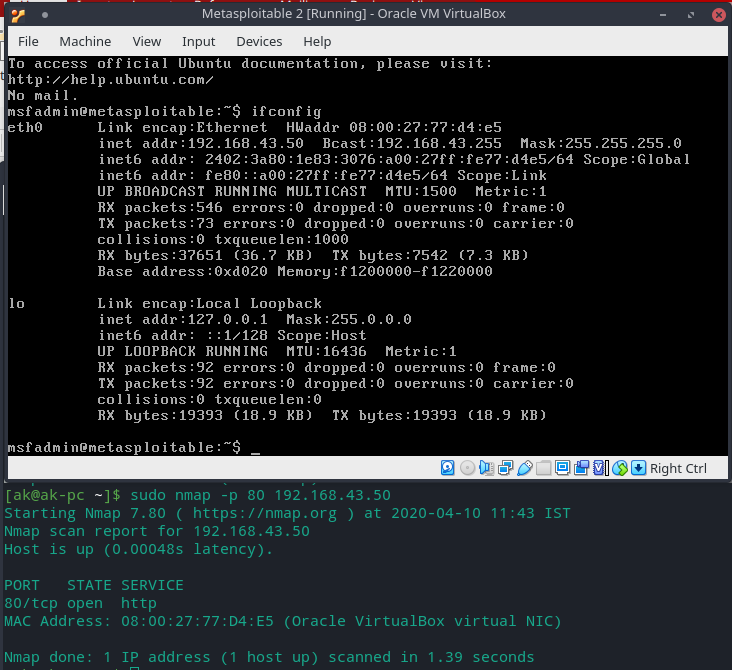
sudo nmap -p [PORT] [TARGET]
Only scan specified ports
Scanning Metasploitable 2 for port 80 (HTTP)
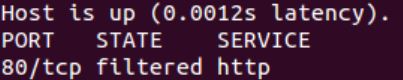
If FILTERED is written under the STATE column it means the port is closed and not accepting connections.
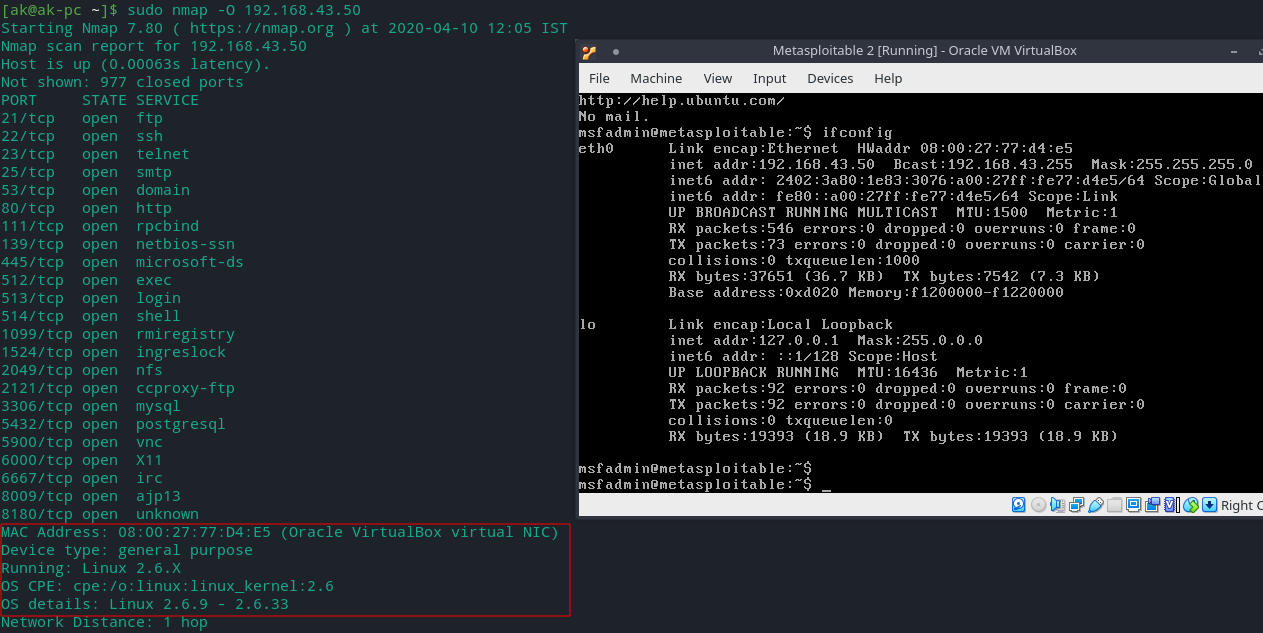
- Identifying operating systems
It will help us to see host operating system and other device type information(MAC address,NIC manufacturer,OS version,device type).We can use this information to find exploits for the host OS.
Syntax
sudo nmap -O [TARGET]
Metasploitable 2 OS identification